Over the last several months, I developed Oildrop (github repo here), a privacy-friendly userscript manager that only contains around 600 lines of JavaScript. It is intended to be user-audited in less than half an hour, so that you can be sure it doesn’t collect your data. For context, most other userscript managers contain tens of thousands of lines of JS.
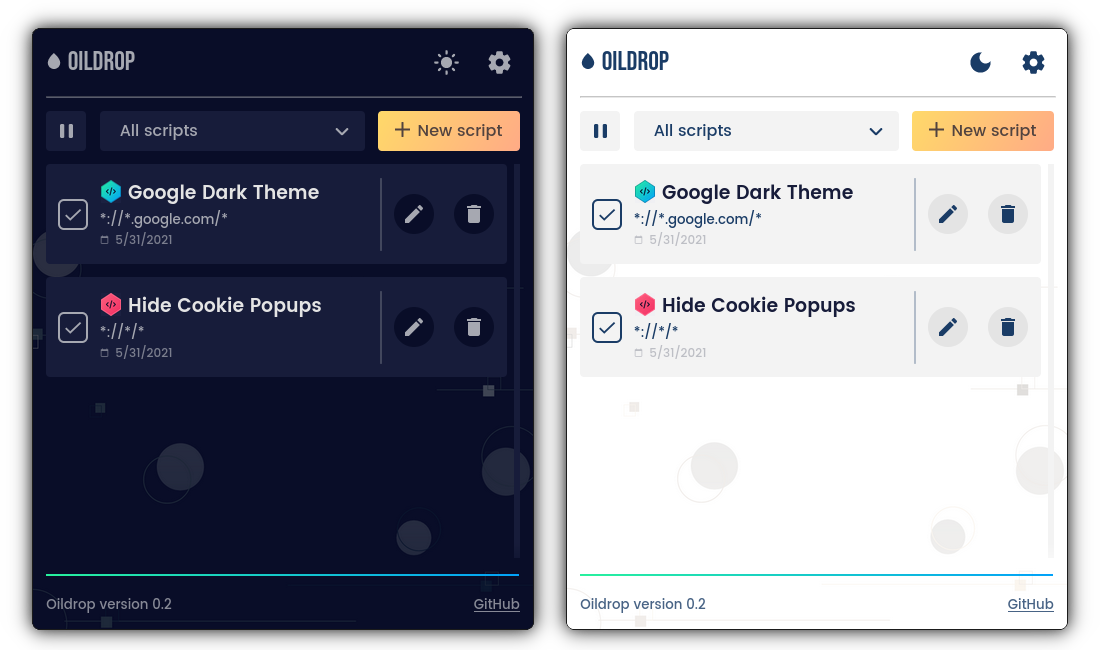 Oildrop is lightweight, accessible, and comes with both a light and a dark mode.
Oildrop is lightweight, accessible, and comes with both a light and a dark mode.
The UI was designed by Chiara Colangelo, a freelance graphic designer who did a fantastic job of making Oildrop pop.
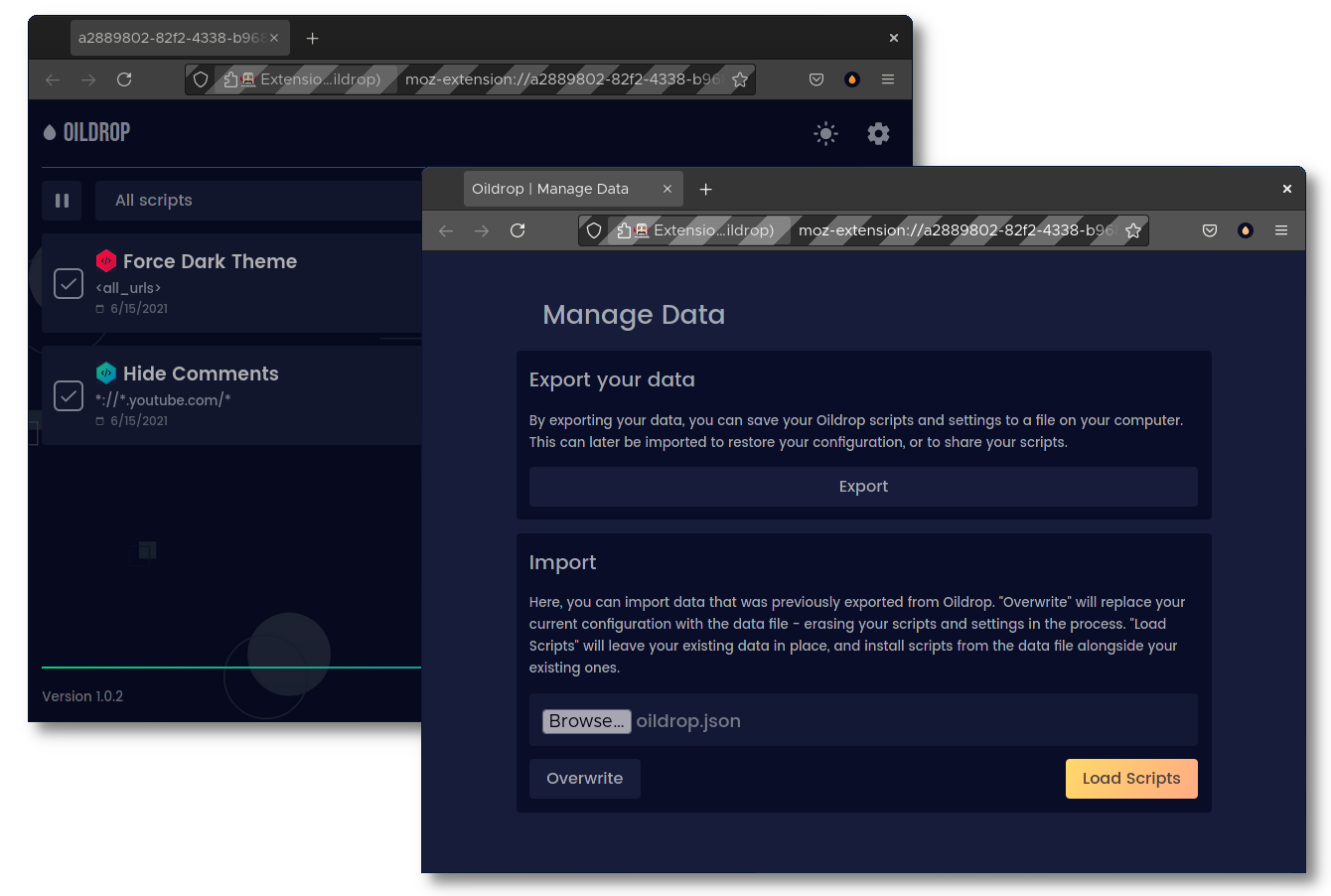 Oildrop can be opened in a window or through its icon, and offers import and export functionality.
Oildrop can be opened in a window or through its icon, and offers import and export functionality.
If you’re curious about why a small codebase is something that is desirable in a browser extension, please continue reading for more context. If you’d like to install Oildrop, it can be found here on the Firefox Addon Store.
Why do Browser Extensions Need so Many Permissions?
Since their inception, browser extensions have been troubled peices of technology. On one hand, they serve a vital use case, enabling users to make choices that are otherwise not afforded to them. On the other hand, they often require extensive permissions which make many privacy conscious users grit their teeth.
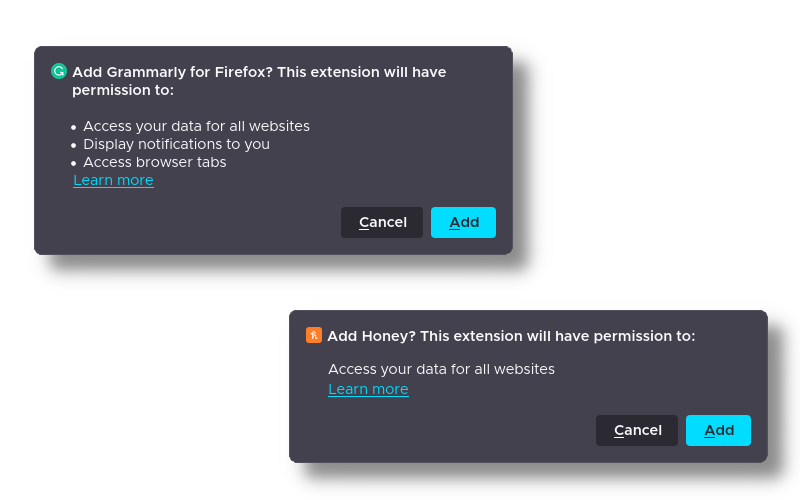 The permission lists for most popular browser extensions seem overreaching. Note that these particular extensions are shown only because they’re popular, and not because they’ve done anything egregious.
The permission lists for most popular browser extensions seem overreaching. Note that these particular extensions are shown only because they’re popular, and not because they’ve done anything egregious.
Does it make you uncomfortable that Honey, a tool that helps you find coupon codes, requires permission to “access your data for all websites?” It makes me uncomfortable. However, I don’t intend to point fingers, and it isn’t just Honey doing this. When you understand the technical details a little better, it’s clear that they don’t have much of a choice in the matter.
Browsers make developers request permissions for access to certain tools, like browser history, downloads, or code injection. They don’t, however, do this at a very granular level. In the case of Honey, they don’t actually want access to “your data for all websites” - they just want to display a nice little widget, and to enter coupon codes in your text field of choice. The problem is all about granularity. The browser has to disable its privacy safeguards to allow that, and so it must warn you that “your data for all websites” is at risk.
Who Should you Trust?
Because even simple browser extensions require such extreme permissions, it can be hard to know if your data is in good hands. Although most browser extensions are harmless, there have been many cases of extension makers abusing these obtuse priveleges to spy on users, and there is no reason to believe that this will stop any time soon.
One of the most notable examples of this happened after SimilarWeb, an analytics company, acquired the userstyle manager Stylish. Userstyle and userscript managers require access to all page and user data as a result of their internal workings, and Stylish was caught using these permissions to silently collect their users’ browser history.
More recently, Avast identified a set of popular browser extensions that contained data collecting malware which was undetected for years even after approval from various extension stores.
As a result, answering this section’s titular question isn’t quite as easy as it sounds. In my opinion, you should trust a browser extension for one of two reasons. Either you have significant trust for its author, or you’ve taken the time to read its source code yourself. The former option is quite easy, but the latter method is the only way you can be sure that the extension is safe.
Oildrop
As a nitpicky software developer, I used to use Stylish and Tampermonkey to modify my commonly used websites. However, after Stylish had its debacle, I realized that I had not been paying enough attention to who I was entrusting my data with.
Additionally, it is very difficult to audit a large browser extension due to their sizes. TamperMonkey has 25 462 lines of JavaScript, GreaseMonkey has 20 784, and ViolentMonkey has 9 539 (measured using csloc).
For most people, that isn’t a problem - these extensions are used by many, and are likely very trustworthy. But for folks trying to be privacy conscious, that’s a big red flag. Nobody can read that much code in a reasonable timeframe.
As a response to this, I developed Oildrop, which is designed to be user-audited as quickly as possible. It uses only 565 lines of JavaScript at the time of writing, and can be easily extended or modified.
To get it that small, I had to make a few sacrifices. It doesn’t support the GM_ API introduced by GreaseMonkey, and it only works on Firefox at the moment. However, it doesn’t spare any expense on look and feel, and you can be completely sure that it isn’t spying on you.
